For a long time now, cybersecurity has been reactive in dealing with indicators or the aftermath. However, threat landscape is evolving rapidly, and it is far beyond what traditional defenses were designed to handle. Today’s advanced threats use lateral movements and living-off-the-land techniques to easily bypass the traditional solutions such as firewalls and signature-based detection.
This reality demands more than a traditional defensive approach. It needs a proactive, attacker-focused approach such as deception technology. It turns your network into traps to lure the lurkers to reveal themselves before they can cause damage.
This blog explores the key advantages of deception technology that makes it a critical component in today’s cybersecurity controls.
What is Deception Technology?
Deception Technology takes a fundamentally different approach to detect threats. It deploys fake assets such as decoy servers, fabricated credentials, fake file shares, dummy databases, and breadcrumb trails that look like valuable targets for the attackers. These mimic the actual assets in the network but serve no legitimate business purpose.
Deception Technology relies on a simple concept that because these fake assets have no authorized authentic users, any interaction with them is suspicious. Thus, when anyone interacts with the decoy or attempts to use fake credentials, or follows the planted breadcrumb, the system immediately triggers an alarm.
Traditional security assumes that attackers can be kept out. Deception Technology assumes that the attackers will breach and work on exposing them faster.
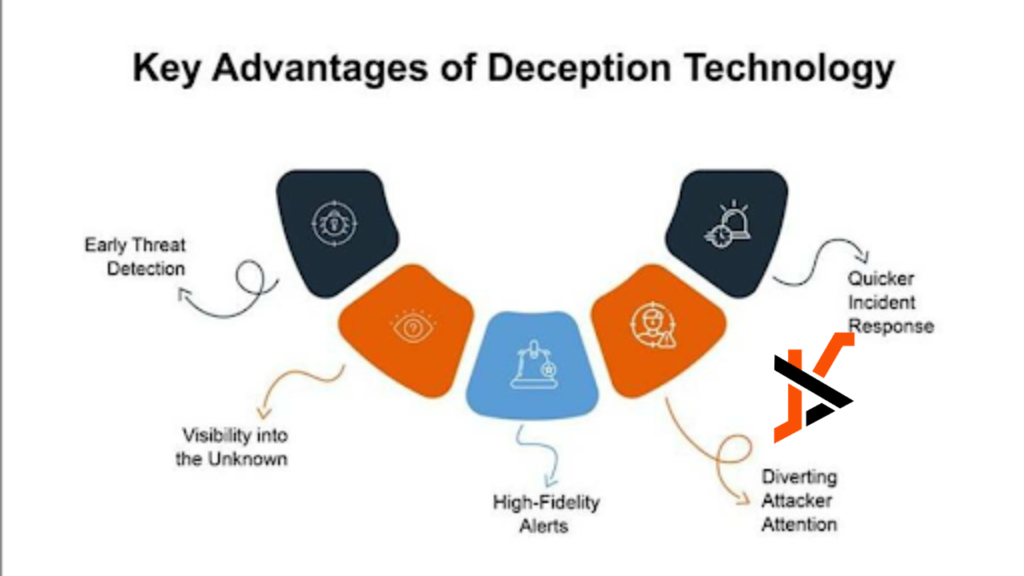
Key Advantages of Deception Technology Over Traditional Cyber Defense Security
Key Advantage #1: Early Threat Detection
Traditional controls often detect threats late in the attack lifecycle viz. after exploitation has occurred, malware has been deployed, or data has already been compromised. In fact, studies suggest that it takes an average of 212 days to detect a data breach. At this stage, response becomes complex and costly.
Deception Technology on the other hand detects threat much earlier in the kill chain. It identifies the attackers during the reconnaissance itself. For example, it exposes attackers when they are scanning valuable targets or harvesting credentials.
Deception Technology can expose the attacker any time across discovery, credential access, lateral movement, or collection stages and maps it with MITRE ATT&CK framework for easy analysis.
This early warning gives defenders precious time to contain threats before they escalate into full-blown breaches.
Key Advantage #2: Visibility into the Unknown
Traditional cyber defense security tools rely on historical data such as signature databases or known indicators of compromise. This creates a dangerous gap and makes the tools struggle against new malware variants, or advanced attackers who can pose as legitimate assets.
Deception Technology does not rely on any kind of traditional threat intelligence. It does not need an insight into what the attack looks like because it focuses on attacker behavior. Whether it is facing a never-seen-before zero-day attack, malicious insider activity, or stealthy ‘living-off-the-land’ techniques that misuse trusted tools like PowerShell or WMI, deception detects them all through unauthorized interaction with fake assets.
This behavior-based approach makes Deception Technology valuable against zero-day, unknown, and advanced threats.
Key Advantage #3: Minimizing False Positives
Security Operations Centers (SOCs) are often bombarded with a high volume of alerts generated by traditional security tools. It is overwhelming for the analysts to quickly identify and prioritize genuine threats.
According to Forrester, SOC teams receive approximately 11,000 alerts daily, and 55% of cloud security professionals admit that they miss critical alerts in the noise.
Deception Technology, on the other hand, largely minimizes this issue. Since legitimate users do not engage with decoy assets, any interaction with them immediately qualifies into high-confidence alerts.
Research shows that deception technology slashes false positives by up to 90%.
This significant reduction in false positives helps bring down the alert fatigue, accelerates investigations, and allows analysts to focus on genuine threats further safeguarding the business.
Key Advantage #4: Diverting Attacker Attention
Deception Technology creates a deceptive attack surface that alters the attacker’s behavior in your network. These fake assets divert their attention from the genuine production systems and valuable assets.
In case the attackers have already intruded and begin their lateral movement, the chances of encountering the decoys increase, immediately revealing their presence and intentions. These features of deception approach prove beneficial in hybrid environments and multi-cloud environments where traditional tools fall short.
Key Advantage #5: Quicker Incident Response
Traditional security tools report their alerts using raw logs, isolated indicators, or statistical anomalies that require further investigation and correlation. Analysts must connect the dots between what happened, reconstruct attack timeline to determine attack intent. These processes are time-taking and consequently delay the actual response to the attack.
Deception Technology provides complete visibility into the attacker’s tactics, techniques, and procedures (TTPs). Analysts gain insights into what asset or credentials were attempted to access and how the lurkers moved across the network.
This context allows the SOCs to respond to the attack almost immediately. With support of a Security Orchestration, Automation, and Response (SOAR) platform, automatic containment workflows can be triggered can automatically helping businesses isolate compromised systems within minutes instead of days or hours.
How Fidelis Security Helps?
Fidelis Deception® helps by deploying decoys and lures throughout your environment, converting your network into an early warning system that catches attackers in real-time. It works seamlessly across on-premises, cloud, and hybrid platforms as well as adapts to your company’s unique architecture and scaling requirements.
In Conclusion
Traditional cyber defense solutions such as firewalls, antivirus, Endpoint Detection & Response are essential for protecting assets. However, they operate reactively and protect majorly against known threat patterns and indicators.
Deception Technology on the other hand helps by proactively exposing malicious activity irrespective of the tools and techniques attackers use.
By focusing on attacker behavior more than the attack signatures, deception changes the security equation fundamentally. As attackers grow more sophisticated, leveraging zero-day exploits, living-off-the-land techniques, and prolonged dwell times, it is high time for security strategies to move beyond passive defense.
The future of cybersecurity lies in asymmetric approaches with a combination of traditional defense security measures as well as deception technology that turn the attacker’s own behaviors against them.