Deception enables a more proactive security act. Deception aims to avoid a cybercriminal that has managed to penetrate a network from doing any huge damage. It offers a more accurate and quicker detection of attackers. It creates no false positives. Honeypots were the first simple form of deception. It is intended to detect existing intrusions and return that breach intelligence directly to the network’s security team. Any other cybersecurity sends a huge amount of alerts for being attacked each alert needs to be solved specifically but a maximum of them are false positives this is too time-consuming and requires more and more employees. So all we need to reduce the false positives alerts but that increases the possibility of false negatives. The potential for false negatives is more effective than false positives, to detect this kind of threats we need to use the Deception Technology.
There are two types of Deception Technology described below.
- Active Deception: Active Deception will provide inaccurate information intentionally to the subjects (intruders or hackers) to fall for the trap.
- Passive Deception: Passive Deception will provide incomplete information, o the other half of information. Intruders will try to gain all the information and will fall for the trap.
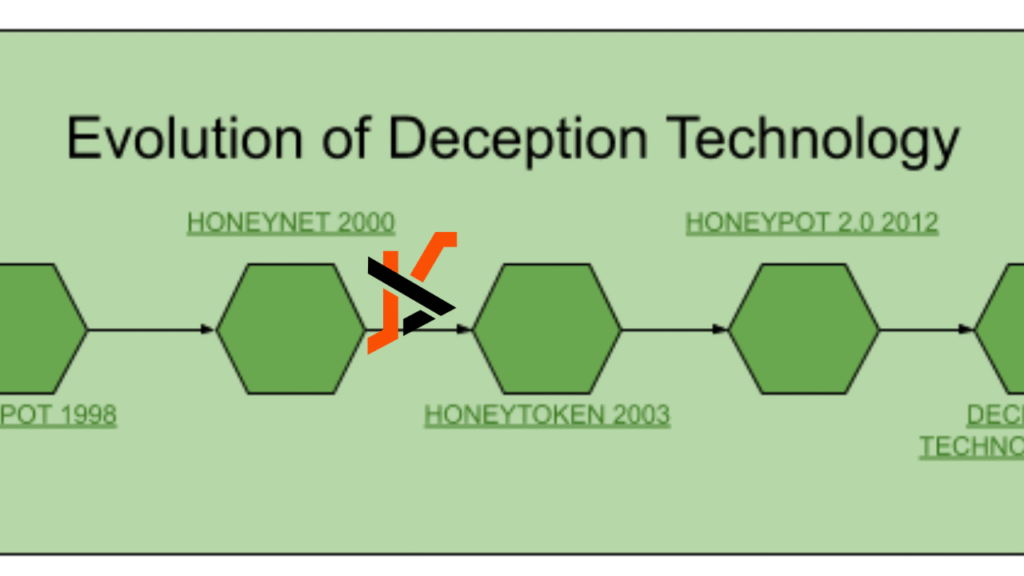
Evolution of Deception Technology:
Working Principle of Deception Technology:
The Deception Technology is for MILDEC or military deception. The Deception Technology’s working principle is much simpler to understand, a false decoy network will run on-existing infrastructure, but not visible by genuine staff. When any hacker or intruder visits that infrastructure they will be able to see the decoy as an opportunity to hack the infrastructure and they will fall for that.
The decoy for the intruder must be simple, so the intruder can easily break through the guard and fall for the trap. The decoy should behave like important information or data for the organization only then the attacker will penetrate the security. The setup of Deception Technology should not be distinguishable by the intruders. Set-up is best done automatically by a system that maps the real network which defines the content and positioning of decoys.
Deception Technology applicable methods:
- Piggybacking: Piggybacking happens when criminal labels along with an authorized person to gain entry into a protected location or a limited region. Unsecured wireless networks can be piggybacked.
- Impersonation: Criminals can undermine the reliability of individuals by using the website and social media posts. Impersonation is the act of pretending as another person with the objective of acquiring data of an individual, organization, and so forth.
- Web-based Deception: Sending hoax emails, jokes, movies, and non-business related emails at work may violate the organization’s acceptable use policy and result in disciplinary activities.
- Shoulder Surfing: Shoulder surfing means acquiring personal data through direct observation. An attacker can use binoculars or circuit cameras for shoulder surfing. The most commonly stolen data through shoulder surfing includes credit card numbers, PINs, access codes, and so on.
- Hoaxes: A hoax is an act intended to deceive. A hoax can cause just the same amount of disturbance as an actual breach would cause. The response can make unnecessary fear and unreasonable behavior. Clients pass hoaxes through email and online networking. A hoax evokes a client response.
Importance of Deception Technology: Deception Technology depends upon recognition of presence rather than known signatures. It will identify all types of intrusion and intruder whether that is a cybercriminal, a contractor doing more than the agreement specifies, or an employee seeking information on an upcoming merger.