In the world of cloud-native applications and Kubernetes, security is a paramount concern. As organizations move their applications to Kubernetes, ensuring secure communication between services becomes essential. One common approach to achieving this is through the use of client certificates. In this article, we will explore how to use Helm generate client certificate, the importance of these certificates, and best practices for managing them.
Helm Generate Client Certificate and Their Importance
Before diving into the process of generating client certificates with Helm, it’s crucial to understand what client certificates are and why they matter.
What are Client Certificates?
Client certificates are a type of digital certificate used to authenticate clients to servers. Unlike server certificates, which validate the identity of the server to clients, client certificates confirm the identity of clients when they connect to servers. This mutual authentication process is essential in environments where security is critical, such as financial institutions, healthcare systems, and any application dealing with sensitive data.
Why Use Client Certificates?
- Enhanced Security: Client certificates provide a higher level of security than traditional username and password authentication. Since the certificate is tied to a specific client, it is much harder for unauthorized users to gain access.
- Mutual Authentication: In many cases, both the client and server need to authenticate each other. Client certificates facilitate this mutual authentication, ensuring that both parties are who they claim to be.
- Non-repudiation: With client certificates, it’s possible to prove that a particular client initiated a connection, reducing the likelihood of disputes over who accessed a service.
- Automation: In cloud environments, the use of client certificates can automate the authentication process between services, enabling seamless communication without manual intervention.
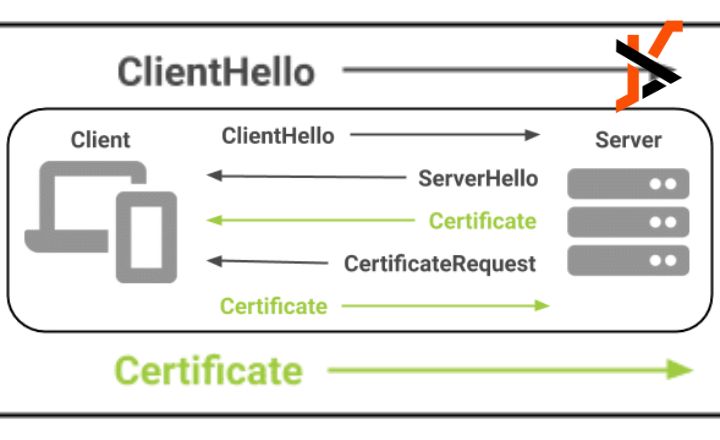
Generating Client Certificates with Helm
Helm is a package manager for Kubernetes that simplifies the deployment and management of applications. To generate client certificates using Helm, you typically rely on a combination of Helm charts and Kubernetes secrets. Here’s a step-by-step guide on how to accomplish this.
Step 1: Set Up Your Environment
Before you start, ensure that you have the following tools installed and configured:
- Kubernetes Cluster: You need access to a Kubernetes cluster where you can deploy your applications.
- Helm: Install Helm on your local machine or wherever you plan to manage your Kubernetes applications.
- OpenSSL: This tool is essential for generating certificates and keys.
Step 2: Create a Helm Chart
If you don’t already have a Helm chart for your application, you can create one using the Helm CLI:
bash
Copy
helm create my-app
cd my-app
This command generates a basic directory structure for your Helm chart.
Step 3: Generate the Client Certificate
Now, we will use OpenSSL to create a client certificate. You will need to generate a private key and then create a certificate signing request (CSR), which will later be signed by a Certificate Authority (CA).
Generate a Private Key:
bash
Copy
openssl genrsa -out client.key 2048
Create a Certificate Signing Request (CSR):
bash
Copy
openssl req -new -key client.key -out client.csr
- During this step, you will be prompted to provide information such as your country, state, organization, and common name. Ensure that the common name is unique to your client.
Self-sign the Certificate (for testing purposes):
If you don’t have a CA, you can self-sign the certificate:
bash
Copy
openssl x509 -req -days 365 -in client.csr -signkey client.key -out client.crt
- This command creates a self-signed certificate valid for 365 days.
Step 4: Create Kubernetes Secrets
Once you have your client certificate and key, the next step is to create Kubernetes secrets to store these securely. You can do this using the following command:
bash
Copy
kubectl create secret tls client-cert –cert=client.crt –key=client.key
This command creates a secret named client-cert that contains your client certificate and private key.
Step 5: Update Your Helm Chart
Now that you have created the Kubernetes secret, you need to reference it in your Helm chart. Open the values.yaml file in your Helm chart directory and add the following section:
yaml
Copy
clientCert:
secretName: client-cert
Next, update your deployment template (found in templates/deployment.yaml) to mount the secret into your application’s pods:
yaml
Copy
apiVersion: apps/v1
kind: Deployment
metadata:
name: {{ .Release.Name }}
spec:
template:
spec:
containers:
– name: my-app
image: my-app-image
volumeMounts:
– name: client-cert
mountPath: /etc/ssl/certs
readOnly: true
volumes:
– name: client-cert
secret:
secretName: {{ .Values.clientCert.secretName }}
This configuration mounts the client certificate into the specified path in your application’s container.
Step 6: Deploy Your Helm Chart
Finally, you can deploy your Helm chart with the following command:
bash
Copy
helm install my-app ./my-app
This command deploys your application, including the client certificate configuration.
Best Practices for Managing Client Certificates
Generating client certificates is just the beginning. Here are some best practices to ensure effective management:
- Regular Rotation: Rotate your client certificates regularly to minimize the risks associated with compromised keys.
- Use a Trusted CA: For production environments, consider using a trusted Certificate Authority to sign your certificates, rather than self-signing.
- Automate Certificate Management: Use tools like Certbot or Kubernetes operators to automate the generation and renewal of certificates.
- Monitor and Audit: Regularly monitor the usage of client certificates and audit access logs to detect any unauthorized access.
- Secure Storage: Store your private keys securely. Use Kubernetes secrets or a dedicated secrets management solution to protect sensitive information.

Troubleshooting Common Issues
While generating client certificates with Helm is straightforward, you may encounter some common issues. Here are a few troubleshooting tips:
1. Certificate Not Recognized
If your application does not recognize the client certificate, ensure that it is properly mounted in the container. Check the mountPath in your deployment configuration and verify that the application is looking for the certificate in the correct location.
2. Expired Certificate
If you receive errors related to expired certificates, it may be time to rotate your client certificates. Implement a schedule for regular certificate renewal and ensure that your application can handle updates without downtime.
3. Permissions Issues
Ensure that your Kubernetes secrets have the correct permissions set. If your application cannot access the secrets, you may need to review the Role-Based Access Control (RBAC) settings in your Kubernetes cluster.
4. Self-Signed Certificate Trust
If you are using a self-signed certificate and your application encounters trust issues, you may need to configure your application to accept self-signed certificates. This often involves adding the certificate to the application’s trust store.
Conclusion
The process to helm generate client certificate is a crucial step in establishing secure communication between services in a Kubernetes environment. By following the steps outlined in this article, you can generate and manage client certificates effectively, enhancing the security of your cloud-native applications.
As security remains a top concern in today’s digital landscape, ensuring that you implement best practices for certificate management will safeguard your applications against potential threats. With the right tools and strategies, you can confidently navigate the complexities of secure communication in Kubernetes.

