What Is Ransomware?
Ransomware is malicious software that stealthily lands on a computer, scrambles or blocks access to local and network-shared data, and then flashes a note demanding payment-almost always in cryptocurrency restore your files. Over the past decade, the crime has matured into a professional ecosystem: developers sell turnkey “kits,” affiliates run the campaigns, and negotiated payments funnel through mixers to mask the cash-out trail. Modern crews also steal sensitive information before they encrypt it; if victims refuse to pay, attackers threaten to leak the data publicly, sue for GDPR violations, or call customers to crank up the pressure.
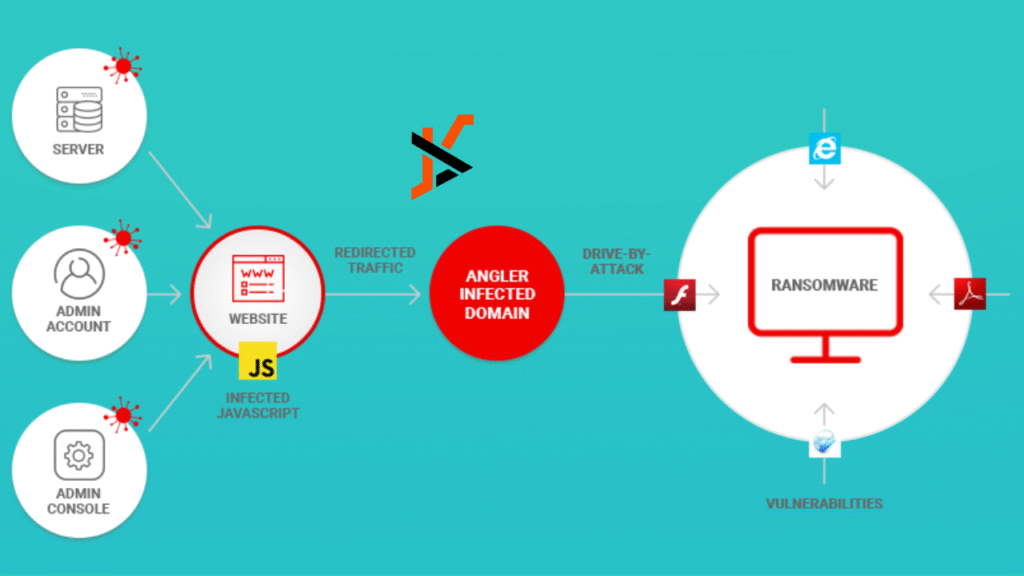
How a Ransomware Attack Unfolds
A typical campaign follows a predictable three-stage playbook:
Initial access comes through weaponized email attachments, phishing links that install droppers, exploitation of unpatched VPN appliances, or brute-forced remote desktop credentials.
Installation and spread begin seconds later. The dropper contacts a command-and-control server, retrieves the main payload, creates back-door persistence, and scans for neighboring systems, shared drives, and hypervisors. Living-off-the-land tools- PowerShell, PsExec, WMIC- keep activity under the radar.
Encryption and extortion are triggered when the operator flips a kill switch. Files receive new extensions, backups are deleted if reachable, and a ransom note appears with deadlines and Bitcoin wallet instructions. Many crews now combine this damage with voice-mail or SMS harassment to executives until payment is sent.
Understanding each phase is crucial, because breaking any single link-for example, blocking macros, patching that VPN, or disabling lateral-movement tools-can collapse the entire campaign before encryption starts.
Fast Facts That Put the Threat in Context
Annual industry reports make one thing clear: Ransomware is no longer a niche worry.
- Average demand in 2024 tops $800,000. Downtime, forensic fees, legal counsel, and brand damage often double that figure, according to the FBI IC3 report.
- More than 70 percent of campaigns now exfiltrate data. Even organizations with pristine backups face blackmail threats.
- Phishing remains the launchpad for roughly 90 percent of incidents. Despite machine-learning filters, one distracted employee can still sink a network.
- Dwell time averages under 24 hours. Automation accelerates lateral spread, giving defenders very little room to breathe.
A subtle but important distinction hides inside those numbers: Many people still conflate any large breach with ransomware. In reality, a breach that steals data without encryption differs from the full hostage scenario. If you want an authoritative primer on what is ransomware attack on a network, including how encryption, exfiltration, and extortion this offers a concise technical deep-dive.
High-Profile Strains to Know About
- LockBit. A “franchise” platform that automates spread, displays live countdown timers, and even offers a support chat for victims.
- BlackCat (ALPHV). Written in Rust, highly modular, and capable of encrypting cloud storage buckets and corporate SharePoint libraries.
- Clop. Specializes in exploiting file-transfer software zero-days, then leaking terabytes of victim data on a public shaming site.
Notably, each strain reuses large chunks of open-source code, reinforcing how low the barrier to entry has become.
Why Ransomware Keeps Growing
- Ransomware-as-a-Service kits. Turnkey portals with dashboards and chat support mean technical skill is no longer a hiring prerequisite for criminals.
- Cryptocurrency. Bitcoin’s pseudonymity and lightning-fast settlement make global extortion feasible.
- High-value targets. Hospitals, municipalities, and supply-chain hubs can’t afford prolonged outages, so they often pay within hours.
- Remote work. Laptops on home Wi-Fi send corporate perimeters sprawling into thousands of living rooms.
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) warns that these factors create a “perfect storm,” and its Stop Ransomware portal now ranks among the most consulted defensive references worldwide.
Prevention Strategies That Really Work
Patch quickly, enable MFA, and harden backups may sound like evergreen advice, yet countless investigations show lapses in exactly these controls. A few implementation tips:
- Patching. Automate with tools such as Windows Update for Business or fleet-wide Linux package managers. Target a 72-hour remediation window for critical CVEs. Microsoft’s Security Blog notes that attackers typically weaponize a new exploit within eight days of disclosure.
- Multi-factor authentication everywhere. Prioritize VPN gateways, privileged cloud consoles, and email platforms. According to Google, MFA thwarts 99 percent of bulk credential-stuffing attacks.
- Offline, immutable backups. Whether tape, cold S3 Glacier, or a WORM appliance, ensure no write/delete privileges for production service accounts. Test monthly restores.
- Quarterly phishing simulations. Services such as KnowBe4 or Cofense reveal click-through rates and guide targeted training.
- Least privilege plus segmentation. Remove local admin rights, restrict service accounts, and place accounting servers in a separate VLAN from marketing laptops.
- Endpoint Detection & Response. Tools that flag mass file-renaming or untrusted PowerShell help neutralize encryption in real time.
- Documented incident-response plan. A playbook with phone trees, crypto-wallet policies, and legal templates saves hours when every minute matters.
The UK National Cyber Security Centre lays out a complementary checklist in its Malware & Ransomware Guidance.
Immediate Actions If the Worst Happens
Pull the network cable first-analysis comes second. MITRE’s ATT&CK framework stresses that early isolation prevents wider infection, especially on flat networks. Notify your breach-coaching counsel and cyber-insurance carrier promptly; some policies include negotiators and forensic services. Collect volatile memory images and system logs before powering off servers. If offline backups exist, verify their integrity with a sandbox restore. When weighing payment, remember that OFAC sanctions prohibit transactions with certain wallets; consult law enforcement, such as the FBI Internet Crime Complaint Center, to avoid inadvertent penalties.
Future Trends on the Horizon
- Triple extortion. Locking data and leaking it are only steps one and two; step three involves harassment of customers or investors to amplify pressure.
- Attacks on backup platforms. New strains target cloud snapshots and on-prem backup servers directly.
- AI-powered phishing. Deep-fake audio asking payroll to change direct-deposit details is no longer theoretical.
- Ransomware in operational technology. Factory floor PLCs and smart-building HVAC controllers are lucrative because downtime threatens safety.
KrebsOnSecurity recently profiled an incident where a European manufacturing plant lost €40 million in halted production after a PLC ransomware infection preview of the stakes for industrial operators.
Conclusion
Ransomware continues to be one of the most disruptive and costly forms of cybercrime, targeting individuals, businesses, and governments alike. Understanding how ransomware works, recognizing the signs of an attack, and implementing robust prevention strategies are critical steps toward safeguarding your digital assets. By staying informed, maintaining regular data backups, updating software, and promoting cybersecurity awareness, organizations and individuals can significantly reduce their risk. As cyber threats evolve, so too must our defenses- proactive vigilance is the best defense against ransomware.
Frequently Asked Questions
Q1: Should I ever pay the ransom?
Paying is a last resort. You may violate regulations, receive a faulty decryptor, or mark yourself as an easy target. Exhaust restoration options and consult law enforcement before considering payment.
Q2: Can antivirus alone stop modern ransomware?
Signature-based antivirus catches known strains, but many campaigns use polymorphic binaries and file-less scripting. Pair AV with behavior-based EDR and strict privilege controls.
Q3: How often should I test my backups?
Industry best practice is monthly validation. Restore a sampling of critical databases and application servers into an isolated environment to verify integrity and recovery time objectives.