SQL injection Prevention Web Medium is one of the most common and dangerous web application vulnerabilities, and it can severely compromise the security of your databases. As more businesses move their operations online, understanding how to prevent SQL injection attacks is crucial. This article will delve into SQL injection prevention strategies tailored for web medium applications, ensuring your data remains safe from malicious attacks.
SQL injection Prevention Web Medium
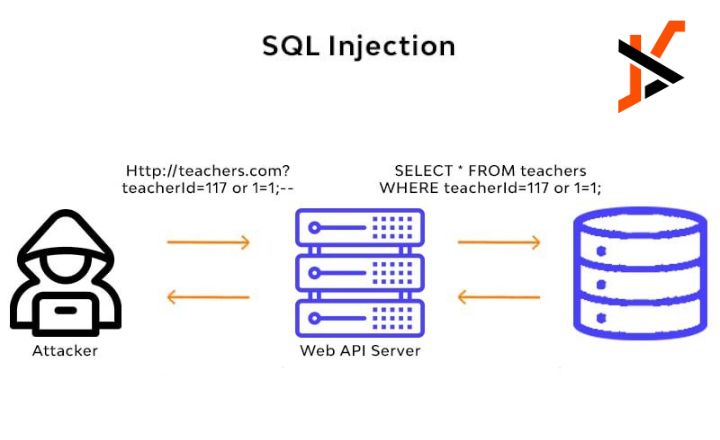
SQL injection occurs when an attacker inserts or “injects” malicious SQL code into a query. This typically happens through input fields that do not properly sanitize user input. If the application fails to filter out harmful code, the attacker can manipulate the database, extract sensitive information, or even delete data.
How SQL Injection Works
To illustrate how SQL injection works, consider a simple login form where users enter their username and password. A typical SQL query for authentication might look like this:
SQL
Copy
SELECT * FROM users WHERE username = ‘user_input’ AND password = ‘user_input’;
If an attacker inputs the following for the username:
SQL
Copy
‘ OR ‘1’=’1
The resulting SQL query becomes:
SQL
Copy
SELECT * FROM users WHERE username = ” OR ‘1’=’1′ AND password = ‘user_input’;
Since ‘1’=’1′ is always true, the database returns all records, potentially granting the attacker access to sensitive information.
The Importance of SQL Injection Prevention in Web Medium
Given the increasing reliance on web applications, SQL injection prevention must be a priority for developers and organizations. A successful SQL injection attack can have devastating repercussions, including data breaches, loss of customer trust, and significant financial losses.

Additional Risks of SQL Injection
Beyond the immediate threats posed by SQL injection, there are additional risks that organizations should consider. One major concern is the potential for data loss or corruption. Successful SQL injection attacks can result in the deletion critical data or unauthorized alterations, which may disrupt business operations.
Moreover, SQL injection can lead to the exposure of sensitive information, such as user credentials, financial data, and personally identifiable information (PII). This can not only harm individuals but also expose organizations to legal liabilities and regulatory penalties, especially in industries governed by strict data protection laws.
Finally, the reputational damage from a successful SQL injection attack can be long-lasting. Customers and clients may lose trust in an organization that has suffered a data breach, leading to decreased customer loyalty and potential loss of revenue.
Key SQL Injection Prevention Techniques
- Prepared Statements and Parameterized Queries
- Prepared statements ensure that SQL code and data are sent separately to the database. This separation prevents attackers from injecting malicious code into the SQL query.
Example in PHP using PDO:
php
Copy
$stmt = $pdo->prepare(“SELECT * FROM users WHERE username = :username AND password = :password”);
$stmt->execute([‘username’ => $user_input_username, ‘password’ => $user_input_password]);
- Stored Procedures
- Stored procedures are precompiled SQL statements stored in the database. They can also help prevent SQL injection by separating the logic from the data.
- However, it’s important to ensure that stored procedures themselves are written securely.
- Input Validation
- Validate and sanitize all user inputs. Use whitelisting techniques to allow only acceptable characters.
- For example, if a username should only contain alphanumeric characters, any input containing symbols should be rejected.
- Escaping User Inputs
- While not a standalone solution, escaping user inputs can add a layer of security. This involves adding a backslash before special characters to ensure they are treated as literals rather than SQL commands.
- Web Application Firewalls (WAF)
- A WAF can act as a barrier between your web application and potential attackers. It can filter out malicious SQL injection attempts before they reach your application.
- Error Handling
- Avoid displaying detailed error messages to users. Instead, implement generic error messages to prevent attackers from gaining insights into your database structure.
- Regular Security Audits and Testing
- Conduct regular security assessments and penetration testing to identify vulnerabilities in your application. Tools can simulate SQL injection attacks to test your defenses.
- Use of ORM Frameworks
- Object-Relational Mapping (ORM) frameworks often handle SQL queries internally, which can reduce the risk of SQL injection. However, it’s still essential to understand how the ORM manages data to ensure secure coding practices.
Implementing SQL Injection Prevention in Web Medium
To effectively implement SQL injection prevention strategies, developers should follow these steps:
Step 1: Educate Your Team
Make sure that all members of your development team understand the risks associated with SQL injection and are trained in best practices for secure coding.
Step 2: Review Existing Code
Conduct a thorough review of existing code to identify any areas where SQL injection vulnerabilities may exist. This includes checking all queries that interact with user inputs.
Step 3: Update Your Frameworks
Keep all frameworks and libraries updated to their latest versions. Many updates include security patches that address known vulnerabilities.
Step 4: Monitor Your Application
Implement monitoring tools that can detect and alert you to unusual database activity, which may indicate an attempted SQL injection attack.
Step 5: Create a Response Plan
Have a clear response plan in case of a successful attack. This plan should include steps for containment, damage assessment, and communication with affected stakeholders.
The Future of SQL Injection Prevention
As technology continues to evolve, the landscape of web security will also change. The rise of machine learning and artificial intelligence offers new opportunities for enhancing SQL injection prevention. These technologies can be used to analyze patterns in user behavior, detect anomalies, and improve threat detection capabilities.
Furthermore, as web applications become more complex, developers will need to adopt secure coding practices as an integral part of the software development lifecycle. This includes integrating security measures from the very beginning of the development process rather than as an afterthought.
Conclusion
SQL injection Prevention Web Medium is a critical aspect of securing web medium applications. By implementing strategies like prepared statements, input validation, and regular security audits, you can significantly reduce the risk of SQL injection attacks. Remember, the cost of prevention is far less than the potential damage caused by a successful attack. For any organization operating online, prioritizing SQL injection prevention should be a fundamental part of your web security strategy. Make it a goal to protect your data and maintain the trust of your users.
By being proactive about SQL injection prevention in your web medium, you not only safeguard your application but also contribute to a safer internet environment for everyone. Furthermore, keeping abreast of emerging security threats and regularly updating your prevention techniques can fortify your defenses. As cyber threats evolve, so must your strategies to combat them, ensuring that your web applications remain resilient against SQL injection and other vulnerabilities.

